Zero-Knowledge Primitives by Aleo

Introducing the core components of any private, programmable application for the Web3 ecosystem. Powered by Aleo.
Zero-Knowledge Technology
In our daily activities online (such as using a search engine or a social network), the amount of data we unnecessarily, irreversibly hand over is a choice we shouldn’t have to make, and it’s in exchange for nothing.
But zero-knowledge provides a potential solution. The ability to prove knowledge without revealing it and to give precise answers to precise questions enhances privacy, increases security, and improves efficiency. It can empower consumers by allowing them to selectively reveal what is relevant for a given application. It can enable companies to enter into partnership agreements without compromising trade secrets. It can ensure compliance with laws and regulations without burdensome surveillance. Overall, ZK opens up a whole new world of opportunity for how we interact and coordinate.
Aleo’s mission is to enable developers to build truly private applications. The cornerstone of our approach is zero-knowledge cryptography, or ZK for short. This technique allows parties on a decentralized network to prove knowledge of some information without revealing the underlying facts that make it true.
A simple metaphor for ZK in action is a bartender verifying a person’s age. They’d typically ask for an ID to check date of birth and match up physical attributes with the person standing in front of them. But the bartender also sees other identifying information on the ID, like a home address. Even though the customer only needs to prove that they are at least of drinking age, they inadvertently reveal much more.
Zero knowledge cryptography would be like enabling a person to prove that they are of legal drinking age without revealing anything else. The bartender can verify this claim with certainty, without even learning the person’s age. This person waiting for a drink at the bar should be able to answer the question “are you of legal drinking age?” with “yes” without revealing any irrelevant personal information.
This technology will create business models that weren’t possible before. These models and their applications will leverage the new capabilities provided by the underlying tech. In the following section, we examine the following building blocks, or primitives, that zero-knowledge cryptography uniquely enables.
Zero-Knowledge Primitives
A “primitive” is a basic building block of a programming language, an atomic unit that is not divisible into smaller components. Applied to a higher, system level, primitives can also be thought of as ingredients, which can be combined in many ways to make different recipes. They are a first-principles approach to emerging technologies, representing the core components of any solution that can be combined and iterated to create novel solutions.
For decentralized finance (DeFi) on Ethereum, an example primitive is a bonding curve, which powers decentralized exchanges like Uniswap. In the nascent Web3 privacy space, identifying useful and unique primitives is a critical first step in the development of private applications.
Blockchains have so far faced a challenge when it comes to reconciling programmability and privacy. Existing solutions either fail to prioritize either, or offer users an unbalanced ratio. On Ethereum and other highly-programmable blockchains, transactions are public and addresses/identities are pseudonymous. Aleo’s zero-knowledge primitives provide a set of core, technical expectations that users and developers can point to for every private, programmable application.
So, what are the primitives of zero-knowledge applications?
Shielded identities are like a firewall which protects the private information of a given person or entity. Remember our bartender example? Shielded identities are like the cryptographically-based driver’s license that hides all irrelevant information from the questioner. Shielded identities allow individuals, smart contracts, DAOs, and enterprises to interact with one another without revealing any information beyond what precisely needs to be known. A simple example is an on-chain know-your-customer (KYC) process for an exchange or dark pool. Unlike in Ethereum, where a user would have to reveal their entire account and complete asset holdings under a pseudonym, shielded identities enable a user to both authenticate to an application yet remain completely anonymous.
Shielded transactions are a primitive first created by Zcash. But shielded transactions in Aleo are more than just asset transfers. They describe all kinds of interactions with another person or program. Some examples beyond simple payments include liquidity provisioning, voting in governance, identity authentication, decentralized notifications, and more. Because only the interacting parties know the details of a transaction, malicious third parties cannot learn the details of that interaction or exploit it in any way.
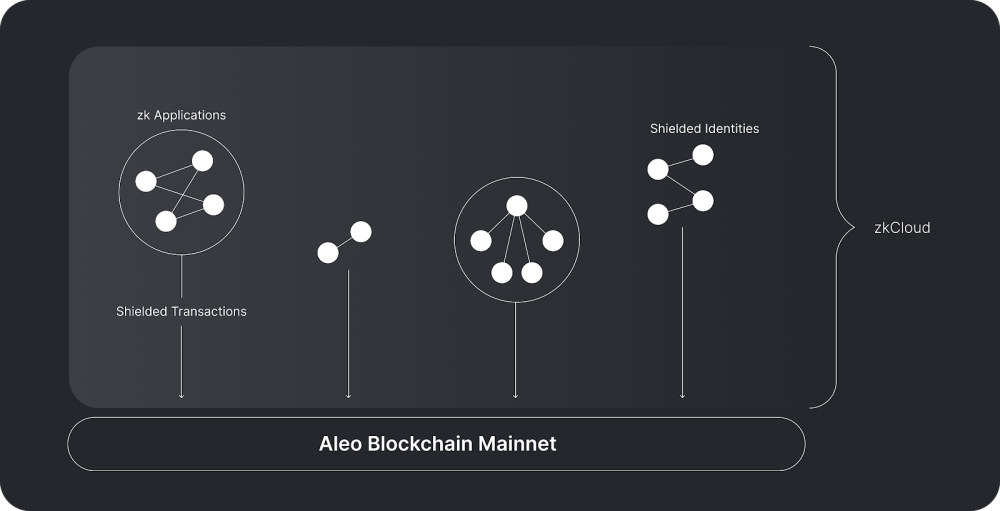
Shielded identities describe the individual(s), and shielded transactions are the means by which they interact. In Aleo, they do so off-chain in an environment we call zkCloud - a component of the Aleo stack that forms the basis for a more secure, private, and personalized paradigm for applications.
zkCloud describes a model of peer-to-peer, decentralized, private computing in which shielded identities interact, either directly (as in an asset transfer) or programmatically (through a smart contract). By moving this interaction off-chain, we not only guarantee privacy, but also enable greater transaction throughput. Shielded transactions link the interactions of one or more parties within zkCloud to the Aleo blockchain. These transactions contain cryptographic proofs that those interactions were valid. Yet by default, they do not disclose what program was executed, or who participated. The Aleo blockchain stores records of these transactions, which can be referenced to determine the global state of an application at any given time.
zkCloud applications can be run locally on a user’s machine, or delegated to a third-party proving-service that constructs proofs and submits transactions on behalf of users. This makes a broader range of applications practical on Aleo today, and opens up the door for a new marketplace for delegated private computation.
To summarize:
zkCloud is the cornerstone of a new model for peer-to-peer, decentralized, private computation that can be either run locally or delegated to specialized provers.
zkCloud enables programmatic interactions between shielded identities, which could be users, organizations, DAOs, or more.
These interactions occur via shielded transactions, which provide cryptographic proofs that guarantee correct execution of a given program.
These transactions are submitted to the Aleo blockchain which updates global state, and anchors the activity on zkCloud and provides a decentralized and censorship-resistant data availability guarantee.
Aleo provides the tools to build truly private applications
Aleo’s core technology stack unlocks the power of these primitives that developers can use to create truly private decentralized applications. If applications can be executed privately, cheaply, and scalably without sacrificing programmability, then a fully private, truly decentralized Web3 ecosystem is within reach. In the next post of our series, we’ll go beyond the primitives of zero-knowledge, and look at what we can do with these building blocks. Stay tuned!
We’re excited to announce that we’ll be publishing a regular newsletter. Subscribing is the best way to stay up to date on the latest Aleo developments and what’s new in ZK. Sign up at aleo.org!
